In the digital economy, securing and allowing access to information only by authorized owners is essential in order to safeguard digital assets. It is not enough to secure the data and the network over which the data passes; it is equally imperative to ensure that only the designated individual can access the assigned account. In a typical setup in most companies, individuals use a user name and a password to connect to a server or website. This approach is incredibly vulnerable. In order to strengthen the security for accessing websites or servers and to reduce the possibility of hacking by unauthorized entities and individuals, multifactor authentication techniques have grown rapidly with most enterprises and individuals. This helps secure digital assets in the wake of cyberattacks, hacking, and heists.
There are three generally accepted factors that are used to establish a digital identity for authentication, including a knowledge factor, which is something that the user knows, such as a password, answers to challenge questions, ID numbers, or a PIN. The second factor is a possession factor: something that the user has, such as a mobile phone or a token. The third factor could be a biometric factor, which is something that the user is, such as his or her fingerprints, eye scan, or voice pattern. Combining two or more such factors allows for reliable authentication. Most 2FA uses the knowledge factor and the possession factor.
There are various 2FA adaptations. In one adaptation, the server sends a message to a mobile device via SMS when someone tries to log in or a voice mail code on any phone. A cell phone has a unique phone number, and it has a physical SIM card inside it that ties it to that phone number with the cell phone provider. However, the phone number is not as secure as one would like to believe. For example, the attacker may call the cell phone company’s customer service department and pretend that the cell phone was lost and the attacker can have your phone number moved to their phone. Thus, the phone number becomes the weak link. Many services allow 2FA to be removed if the phone is lost.
The other adaptation of 2FA is technology such as Google Authenticator, which generates a unique Time-based One-time Password (TOTP) or code on a mobile device that matches one generated simultaneously on a web service’s server. A TOTP verifies user identity based on a shared secret. This secret must be shared online between the user and the provider. While TOTP is simple to use, it has certain shortcomings. The user and the provider server share the same secret. If an attacker is able to hack into the provider server and is able to obtain the password and the secret database, the attacker can access all the accounts. Additionally, the secret is displayed in plain text or as a QR code. This also means that the secret is most likely stored in plain text form on the server of the provider. Basically, one needs to trust that the provider can protect the secret. Most TOTP systems are also susceptible to real-time replay and social engineering attacks and are also indirectly susceptible to man in the middle (MITM) and man in the browser (MITB) attacks.
In addition to TOTP, another approach is based on a Universal Second Factor (U2F). The U2F standard was created by the FIDO Alliance. U2F uses public key cryptography to verify user identity. In contrast with TOTP, users are the only one to know the secret(i.e., the private key). The server sends a challenge, which is then signed by the secret (private key). The resulting message is sent back to the server, which can verify the identity by using the user’s public key in its database.
In one approach, the U2F protocol has been implemented using a USB token device that features a button to activate the device. The server sends a challenge request to the client’s web browser, and then the browser sends the request to the USB device. Once activated, the device signs the challenge and returns the signed data back to the browser, which forwards it back to the server. However, U2F is not going to solve all cybersecurity problems. For example, researchers recently uncovered some flaws in the USB design specifications that may leave firmware unprotected and potentially allow attackers to overwrite firmware and take control of USB devices. This firmware vulnerability could allow USB devices to be reprogrammed to steal the contents of anything written to the drives and spread malicious code to any computer to which these devices are connected. USB malware can potentially infect systems and easily replicate itself and spread to other devices. These dangers are underscored by the fact that they are essentially undetectable. Of course, some USB devices do not have reprogrammable firmware, so not every device may be vulnerable in this way. However, even if the firmware is intact, USB is still highly vulnerable because an otherwise ‘clean’ and uninfected USB device can potentially become infected by being connected to a computer that has been compromised by malware. Thus, the potential risks of USB technology are not limited to firmware vulnerabilities only. The mere use and availability of USB connections and devices poses similar, disturbing data security risks. This is why experts such as the United States Computer Emergency Readiness Team (US-CERT) recommend that users never connect USB devices to untrustworthy machines such as public computer kiosks and never connect them to home or enterprise systems unless they know and trust every connection that the device has ever made. This is why most defense agencies and defense contractors only buy computers that do not have any USB connections. Their employees thus cannot use USB authentication.
Instead of using the knowledge factor and the possession factor, one can also use the third factor such as a biometric factor, which is something that the user is, such as his or her fingerprints, eye scan, or voice pattern. While the biometric factor is the most convincing way to prove an individual’s identity, it has several drawbacks. Biometric authentication is a “what you are” factor and is based on unique individual characteristics. Physical biometrics includes fingerprints, facial recognition, and eye scans (iris, retina). Behavioral biometrics includes voice recognition and handwritten signatures.
However, biometric authentication systems are not 100% accurate. Environment and usage can affect biometric measurements. They cannot be reset once compromised and you cannot revoke the fingerprint, eye scan, or voice print remotely. A thief could steal the smartphone, create a fake finger, and then use it to unlock the phone at will. It has also been found that master fingerprints can trick many phones and scanners. In one of the biggest hacks ever, the US Office of Personnel Management leaked 5.6 million employee fingerprints. For the people involved, a part of their identity will always be compromised. Unlike passwords, fingerprints last a lifetime and are usually associated with critical identities. Thus, the leakage of fingerprints is irredeemable.
Tricking an eye scanner may require taking a photo with a cheap camera in night mode, or getting access to the hacked data from a site that stores the eye scan data. After printing the eye on paper, a wet contact lens is put over it to mimic the roundness of the human eye.
At times, third party authentication services are used to authenticate a user. For example, OpenID is a way of identifying a user, nomatter which web site they visit. Web sites that take advantage of OpenID need not ask for the same information over and over again. However, Open ID alone does not guarantee security, because it still remains the single point of failure. The other approach used by some websites is OAuth for authorization and partial authentication.
However, because OAuth was not designed with this use case in mind, making this assumption can lead to major security flaws. The OAuth communication protocol is not secure and the user can be improperly tricked such that an attacker can obtain his/her credentials.
Therefore, sophisticated attackers are capable of breaking the present multifactor authentication and the third party ID provider’s services. Thus, there is a clear need to come up with a better approach to secure physical and digital assets from cyberattacks, hacking, and heists while providing authentication and authorization in a secure manner.
Zortag has invented a unique technology that combines a 2-dimensional (2D) barcode or RFID chip with randomly distributed 3-dimensional (3D) particles in the form of an optical fingerprint as a unique highly secure identifier. The number of possible combinations of randomly distributed 3D particles within the 3D optical fingerprint exceeds 1060, putting it in the same class as human DNA combinations. These unique combinations are almost impossible to be duplicated by anyone, including Zortag itself. Such 3D elements also have characteristic colors for subsequent image processing and analysis, which further enhance the randomness of this fingerprint structure.
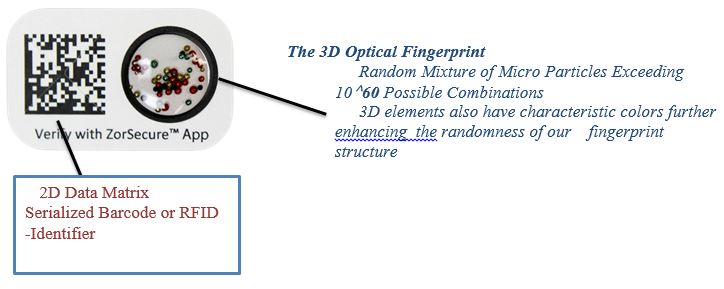
One embodiment of this technology allows for the creation of a Unique Identity and Authentication Key (UIAK) by incorporating Zortag’s 3 D optical finger print in a physical card or key fob and an identity number encoded in a barcode or RFID. UIAK in the form of a physical item such as a card or key fob is almost impossible to be cloned by anyone including Zortag. This UIAK is configured to work only with an authorized mobile device in possession of the user. The unique key and the authorized mobile device together constitute the necessary pair required to access digital assets in a secure manner, making it almost impossible to breach the cybersecurity. This unique pair can identify and authenticate a user and allow access to a website, server, or digital asset in a secure manner. The access can also be limited to a specific geolocation and time period. This platform opens opportunities for companies and individuals to build their own applications where unique identification and authentication of a user or item is critical

Most mobile devices are further protected either by biometrics such as fingerprints, or by eye scans, or by multi-digit passcodes. Unless the user uses one of these to open the mobile device, then the device cannot be used to scan the UIAK. The user may also add another optional level of security in the form of something that only the user knows, such as a passcode or password. This physical UIAK is extremely hard to clone, if not impossible, and this key is not prone to any virus or other types of attack as is the case with software-based keys or USB devices. The security can be further enhanced by having multiple UIAK keys and multiple mobile devices in order to access a digital asset. This is especially applicable in highly secure applications. For example, two keys A and B may be provided, and one mobile device X may be authorized to read key A, and another mobile device Y may be authorized to read key B. In this example, only when this combination is used, will access be authorized to a server.
The UIAK key and the mobile device together constitute the requisite pair of keys, and both of these keys are necessary for the system and process to work. One without the other will not allow the process to go forward. The arrangement of matching the mobile device and the unique identity item can be visualized as having two physical keys that are in the possession of the user and as a pair cannot be hacked.
Unique Identity and Authentication Key (UIAK) or key in the form of a physical item, card, key fob, or single identifying article can also serve as a credit/debit card, health card, ID card, government benefit card, loyalty card, etc., and can also be used as an item that uniquely qualifies a user, allowing a multifactor authentication to access a website or server without a password.
Fundamental Interactions and Velocity Ledger are working with Zortag to implement a unique approach to address the management of cryptocurrencies such as bitcoins by using UIAK and the mobile device pair.
In order to spend the bitcoin, two pieces of information are needed: the public information and the private or secret information. The public information identifies the identity of the coin and its worth and goes on the block chain. The public key is also the address of the bitcoin or asset where the coin needs to be sent. The secret information is the private key of the owner. The private key must be kept secret and protected.
In order to manage the private key, three considerations must be kept in mind. First, the availability to spend the cryptoasset when needed; second, the convenience of managing the key; and third, the security of the key, are some of the key criteria to manage. One way to manage the private key is to store it on a file on local storage media, such as a mobile phone or a computer hard disk or any other device under the control of the owner. It is easily available and convenient to manage. However, if the storage media is lost or stolen, or becomes infected with malware, the asset will be lost. Theft of cryptocurrencies is also not uncommon.
Thus, storing cryptocurrencies on a computer or local devices known as hot storage is fraught with dangers. Also, any device connected to the internet is subject to being hacked and thus not secure. One way to manage this is to store the cryptocurrencies offline or what is called cold storage. Cold storage is not connected to the internet. This may not be convenient, but it is more secure. In this manner, one can keep some asset in hot storage for convenience, but most of it in cold storage for security. One can move asset between cold storage and hot storage and vice versa. In order to manage hot and cold storage, the private keys must be different for each storage. Otherwise, hacking the hot storage private key will also compromise the cold storage private key. Each side also will need to know the public addresses in order to move the cryptocurrencies. There are various ways to manage the addresses for cold and hot storages and moving the asset back and forth.
However, if the private keys of the hot storage or cold storage are hacked, the cryptoasset will be lost forever. Most of the keys are stored in a single place, whether in a safe, in software, on paper, in a computer, or in a device. This creates a single point of failure. If the single point of failure is compromised, then it becomes a problem. While there are ways to avoid single points of failure by splitting the key secrets and storing them at different places, it does create inconvenience and extra overhead.
The Zortag solution technology provides a solution to insure that the private key indeed belongs to the owner who owns the private key. The private key may be stored in a storage media, such as a local device or a server, or in the cloud, etc. It is the access to the storage media that should not be accessible to a hacker. The technology prevents access to the storage media for anyone other than the owner of that storage media. The access to the media is restricted only through Zortag’s Unique Identity and Authentication Key (UIAK) and the authorized mobile reading device. The storage media requests the owner of the private key to scan UIAK by the authorized mobile device, e.g. smart phone. The scanned images and the device information, and the geolocation coordinates of the scanning mobile device and the authorized time during which the scanning is allowed are all sent to an authentication server that checks the authenticity of the UIAK and the device ID, the geolocation data, and the time of scan. If all these parameters are confirmed, the owner is provided access to the media storage to access the private key.
About Satya Sharma
Dr. Sharma is the CEO and President of Zortag. He is also the Executive Director of the Center of Excellence in Wireless and Information Technology at Stony Brook University. Previously, he was Senior Vice President at Symbol Technologies – responsible for mobile computing and wireless engineering and Head of Symbol’s Worldwide Operations in the US, India, Mexico, Japan and China. He was also the Chief Strategy Officer of Symbol. During Dr. Sharma’s tenure at Symbol, the company won the National Medal of Technology from President Clinton in the year 2000. He was also former Global President of Bilcare Technologies. Dr. Sharma was Director at Bell Labs and led AT&T Power Systems to win the prestigious Deming Prize – First for any technology company in the Western Hemisphere. He established Symbol’s software center in India and its manufacturing operation in Mexico. Dr. Sharma holds More than 20 patents and author of more than 75 papers. He is a Member of the Board of Directors of three privately held high technology companies in high speed computing and healthcare and advisor to several start- up companies.
About Julian Jacobson
Julian Jacobson is the Co-Founder, President and Chief Operating Officer of Fundamental Interactions. He has over 20 years of experience in electronic trading industry. Prior to joining Fundamental Interactions, Mr. Jacobson lead sales initiatives at Mantara Inc, where he pioneered institutional sales channels with several of the largest global prime brokers. Prior to this Mr. Jacobson was a senior sales executive at RealTick, a leading provider of global execution management systems which was owned by Lehman Brothers and Barclays Capital during Mr. Jacobson’s tenure there. Mr. Jacobson earned an MBA from the Kelley School of Business in Marketing and Finance.










