If we’ve learned anything from the hacks and breaches in 2018 (think Facebook, Under Armour and Adidas — to name a few) it’s that the business world still struggles to keep up with fraudsters who are exploiting new surface areas and the latest tools to block them. To help shed some light here, our team at Sift Science recently shared our Fraud Myths Report to show how counter-intuitive insights drive better, immediate, automated business decisions. The myths were derived from analyzing 165 billion transactions and 16K signals across Sift Science’s global network.
This article takes a deeper look at four myths from the report affecting the payments and ecommerce industries. Debunking these myths will help businesses understand how fraud misconceptions affect their bottom line and how fraud-fighting tools and insights can help them stay on track to better detect and prevent fraud.
Myth: Fraudsters make small purchases to fly below the radar
People often think businesses don’t allow users to make large purchases without first going through extra security verification. They also assume that fraudsters keep their purchases small to avoid detection. Our research, looking at our customers’ transactions over a 12 month period, showed that a good order typically comes to around $910. The average fraudulent order, by contrast, amounts to about $3,300.
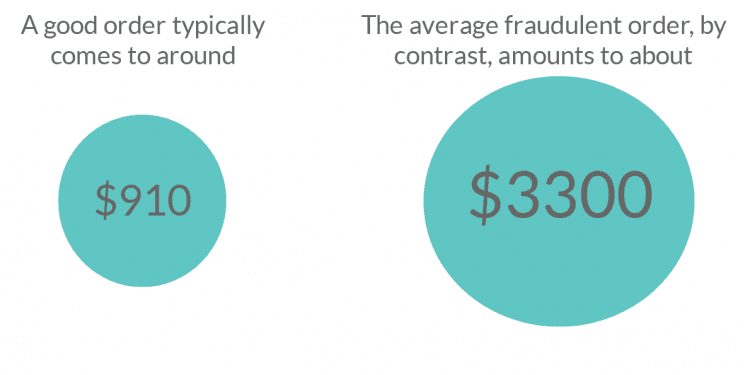
While the first transaction a fraudster makes may be smaller, the reality is that once it works, they make larger purchases in an attempt to extract the maximum value they can out of something like a stolen credit card.
Myth: After committing account takeover (ATO), fraudsters lie in wait for a while before using the stolen account
It’s assumed that ATO quickly arouses suspicion, so fraudsters don’t do anything with a user’s stolen account credentials until they feel the coast is clear. However, ATOs don’t cause suspicion nearly as often or as quickly as people think. In reality, once fraudsters have stolen account credentials, they start making purchases or executing other fraudulent behavior immediately. There may be some slow burner accounts being kept in hibernation, but that’s not the norm and the vast majority of these purchases are done ASAP.
For businesses that experience the highest rates of ATO, a compromised user’s monetary transactions increases an average of 22x within a week of the takeover. Because this increase will eventually raise a red flag for a business, fraudsters use stolen credentials as much and as quickly as they can before the user or business notices and redeems control of the account.
Myth: Activity from ATO is just a blip on a user’s overall transaction history.
The damage overall is often thought to be fairly small and relatively contained in a short period of time, so it’s ultimately insignificant — just a few small fraudulent purchases. A difficult challenge has been understanding and quantifying losses from an ATO, both from a financial standpoint and in long-term value. While in the short term businesses have to deal with the specific fraudulent transactions or activities at hand, they are at risk of losing the entire long-term value of that customer over a single hack.
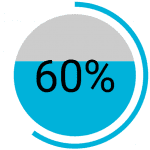
After an ATO, a fraudster’s activity represents up to 60% of the user’s annual spending. This holds true even if a fraudster only has control of a user’s account for a week. What’s more is there can be major financial implications for the user, such as chargebacks, reduced customer engagement and clean-up costs caused by brand damage that can also seriously damages a businesses’ reputation.
Myth: Fraudsters use stolen account credentials once or a few times after an ATO.
A highly dangerous misconception, many users and businesses assume fraudsters will stop using stolen account credentials once they’ve made a few transactions. It’s thought that fraudsters do this to avoid raising red flags by continuing account use, or given the success and frequency of data breaches, that new credentials are readily available to them. However, fraudsters aren’t worried about raising the alarm. If they can get away with it for any period of time, they’ll keep using stolen accounts and credentials until someone notices and takes action.
This might be a few days or a few weeks, but fraud is a full-time job, so a lot of damage can be done even in 24-48 hours. Even 300 days after an ATO, affected businesses may see spikes in median transaction value on stolen accounts. This is why having adaptive, real-time systems in place that limit your exposure rate by identifying account takeovers as they happen, rather than static rules-based systems, is key.
Several things are clear from these findings. Assumptions users and companies are making around ATO and fraud in general play a major role in how businesses shape their fraud-fighting strategies and operations. It highlights the need and importance of using advancing and emerging technologies, for example, in machine learning and behavior analytics, drawing full data and insights from users to better protect and grow your business. These technologies determine things like — how a company’s analysts set up rules for detecting fraud, plus how many people are staffed on the fraud team and brought in on a single day.
If you’re working off of incorrect information and assumptions, then you aren’t properly armed with the right tools and people to protect customers from an account takeover, security breach or fraud hack. Fraudsters continue to get more sophisticated and are becoming harder to fight as the digital space expands. Data, accurate data with real-time insights on next steps and actions, is the key to arming up in the fight against fraud.










