First, you were identified by how you held your phone, typed, and moved the mouse. Then you were recognized by how you browsed and transacted on the website.
AI models have now been tuned to recognize customer coercion. It doesn’t stop there: AI can detect behavior that suggests older adult account abuse, individuals that are mules for criminals, and a range of other previously impossible to detect financial crimes:
This is where the power of behavioural biometrics comes into play. Even though it is a genuine user making the payment, when a person is acting under the influence of a cybercriminal, there are subtle changes in digital behaviour that are statistically significant enough to suggest a social engineering scam may be at play. Some of the behavioural insights obtained from the data collected can help build a picture of a user’s emotions during a session. Figure 1 below summarises a few of the behaviours victims of social engineering scams can exhibit during a session and how these can be interpreted.
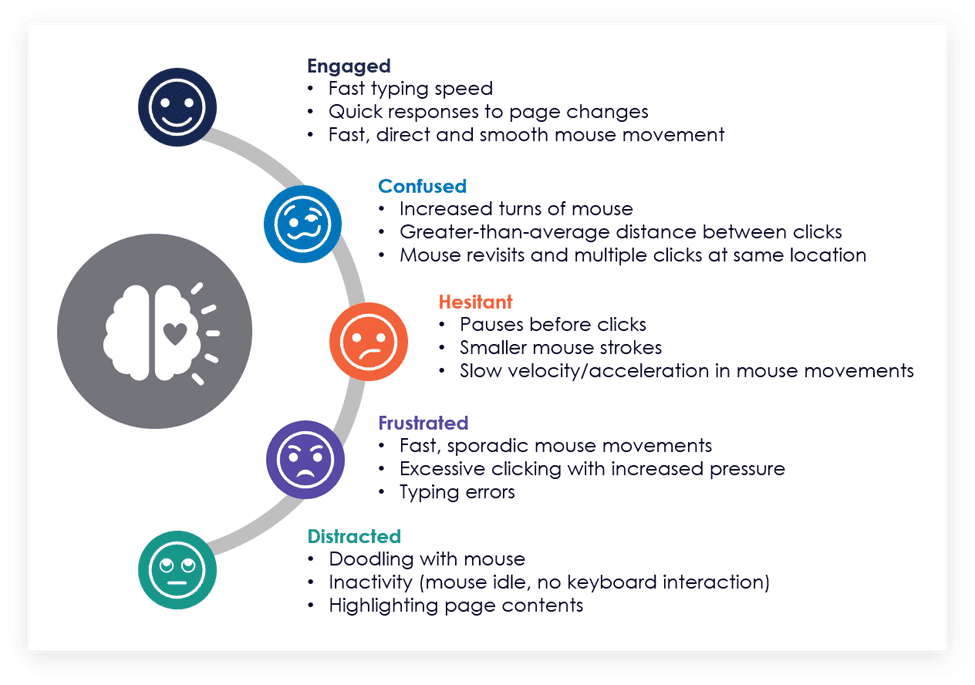
Figure 1: Digital behaviours that indicate a social engineering scam may be occurring in real timeEach individual behaviour on its own does not imply social engineering, but when combined with hundreds of other data points and compared against the norms of the genuine population, these insights have the potential to paint a disturbing picture. Consider something as simple as a customer who is on an active phone call while navigating a live session in a mobile banking app. Analysing the values for this one indicator, there is a significant difference between the genuine and fraud population:
• Less than 1% of all Android users multitask, combining a phone call with mobile banking activity;
• More than 1 in 4 confirmed cases of fraud show that the victim was on an active phone call;
• Data shows that an active call is 30 times more prevalent in the fraud population than the genuine population.
When considering these differences, an active call during a live banking session can be used with other data points as a strong indicator of social engineering.”
Overview by Tim Sloane, VP, Payments Innovation at Mercator Advisory Group










