Mobile devices now constitute the majority of web traffic globally, and consumers are embracing mobile banking in record numbers. Meeting customer demand for mobile banking presents opportunities for banks to differentiate themselves – but providing mobile banking applications also entails significant risk.
SC Magazine reported that an analysis of mobile applications from 50 of the world’s top 100 banks found all to be vulnerable to several security threats. In fact, the apps had an average of seven security flaws, and put half a billion mobile banking customers at risk.
Mobile strategies that mitigate security risks and provide safer transactions will gain a significant advantage in the highly competitive and fast-growing marketplace for mobile banking.
Mobile Banking Is a Big Business…
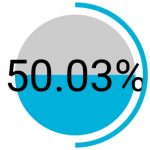
The mobile tipping point—the point at which more people used mobile devices to access the web than desktop devices—came in the first quarter of 2017, when 50.03 percent of global web traffic was from mobile devices.
Banking has been squarely in the center of the mobile evolution. Business Insider described the situation succinctly, noting that mobile banking is “all but required — millennials, for example, will leave financial institutions that don’t offer the service.”
Think of this as the tip of the iceberg. Projections vary, but the number of mobile banking users globally is predicted to double to 1.8 billion by 2019, with Juniper Research anticipating that over 2 billion mobile users—one in three adults globally—will have used their devices for banking purposes by the end of 2021.
…And a Big Target
Unfortunately, the market’s enthusiastic embrace of mobile banking has made apps and users attractive targets for cybercriminals. Already, 60 percent of mobile malware specifically targets financial information. The sheer volume of mobile transactions has already passed critical mass and has made attacks on mobile banking applications a priority for attackers. Even in this relatively early stage of mobile adoption, smartphone users log into their mobile banking apps an average of 18 times per month.
As app capabilities expand, mobile banking activity will continue to increase, and the corresponding surface area that cybercriminals can attack will grow along with it. But the reality is that mobile banking applications already have significant vulnerabilities today.
The Security Challenges of Mobile Banking Development
Accenture reports that one in four mobile banking applications today includes at least one high-risk security flaw.
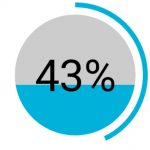
It also found that 35 percent of communications sent by mobile devices are unencrypted and 43 percent of mobile device users do not use a passcode, PIN or pattern lock.
Additionally, in a recent survey by Credit Union Times, 61 percent of respondents saw improving the security of apps and websites as one of their main priorities. How can it be that even security-savvy banks struggle to deliver mobile application security? The simple fact is that customer demand for mobile banking is far outpacing the industry’s ability to deliver ironclad security in the quickly evolving mobile device ecosystem.
Mobile application developers face significant pressure from two different market forces. First, customer demand and competitive pressure are both stronger than ever before. Customers continue to show a huge appetite for expanding their use of mobile banking. To keep up with customers, developers often focus on features rather than security. As deadlines loom, development shortcuts become more appealing, and developers will at times use unvetted, open source code for mobile functions.
Second, while surveys consistently show that mobile banking customers value security in principle, most do not prioritize security in practice. As noted earlier, many mobile device users do not follow essential security practices such as the use of PIN codes or updating to the latest operating system. This exacerbates any vulnerabilities that developers inadvertently allow into their banking applications.
Attack Goals
All of the challenges that mobile banking application developers face can create vulnerabilities for cybercriminals to exploit. Although this is by no means a comprehensive list, consider the following targets for cybercriminals:
- Credentials / Access. Attackers may seek users’ mobile banking credentials to access accounts and commit theft.
- Personal data. Cybercriminals focus on potentially high-value customer data such as social security numbers, dates of birth and other sensitive information.
- Cardholder data. Mobile banking attacks can seek to gather card-specific data such as card numbers, expiration date information and CVV data.
In addition to data, the common goal across attacks is ultimately to compromise and gain control of the mobile device itself. Cybercriminals aim to compromise devices—via malware, network-based attacks, phishing, etc.—so that they have long-term access and ongoing opportunities to do more damage.
Moving Forward: How We Can Properly Defend Mobile Apps and Sessions
Banks must overcome the barriers to mobile banking security by securing mobile banking applications themselves. They must also account for the reality of consumer devices and networks that are far from clean.
Banks should implement basic security measures such as app shielding, obfuscation and encryption. Mobile banking apps also need to be defended against the unclean and dangerous consumer devices upon which they are installed. Mobile apps need self-defense capabilities, such as the ability to detect if a user’s device is compromised, if any network attacks are occurring and even if malicious apps like BankBot are installed. Once the app determines that a device is under attack, it should initiate predetermined risk mitigation actions. Here are a few examples:
- If a man-in-the-middle (MITM) attack is occurring, the app should automatically establish a VPN to create a secure tunnel.
- If a device has phishing malware like BankBot installed, the app should trigger immediate steps to freeze access until the user resets their password online.
- If a device has been “jailbroken” by the user, the app should allow the session to continue, but raise the user’s fraud score to account for the additional risk.
- If a device has been compromised by an external actor, the app should display
a dialog box asking the user to complete their transaction offline.
With self-defense security embedded in mobile apps, banks can focus development efforts on innovations that will delight customers and increase customer loyalty.











